Topic perimeter check: A perimeter check is crucial for maintaining security and accuracy across various domains, including physical security, mathematics, and network management. This comprehensive guide explores the significance, methodologies, and best practices of perimeter checks to help you safeguard your assets, ensure mathematical precision, and protect your network infrastructure effectively.
Table of Content
- Understanding Perimeter Check
- Introduction to Perimeter Check
- Types of Perimeter Checks
- Physical Security Perimeter
- Electronic Security Measures
- Geometric Shapes and Perimeter Calculation
- Real-world Applications of Perimeter in Math
- Network Security Basics
- Firewalls and Intrusion Detection Systems
- Vulnerability Assessments
- Steps for Conducting a Perimeter Check
- Planning and Preparation
- Execution and Monitoring
- Review and Analysis
- Tools and Technologies for Perimeter Checks
- Security Tools
- Mathematical Tools
- Network Security Tools
- Best Practices for Effective Perimeter Checks
- YOUTUBE:
Understanding Perimeter Check
The concept of a perimeter check is essential in various fields such as security, mathematics, and network management. Here, we explore its different applications and significance.
Security Perimeter Check
In the context of security, a perimeter check involves inspecting the boundaries of a secure area to ensure no breaches or unauthorized entries. This is critical for the protection of physical assets and personnel. Key activities include:
- Regular patrolling of the perimeter
- Inspection of fences, gates, and barriers
- Monitoring surveillance cameras
- Checking for signs of tampering or forced entry
Mathematical Perimeter Check
In mathematics, a perimeter check refers to calculating the boundary length of geometric shapes. This is crucial in geometry for determining the size of a figure. The formulas for common shapes are:
- Rectangle: \( P = 2(l + w) \)
- Square: \( P = 4s \)
- Circle: \( P = 2\pi r \)
- Triangle: \( P = a + b + c \)
Where \( P \) is the perimeter, \( l \) and \( w \) are the length and width of the rectangle, \( s \) is the side of the square, \( r \) is the radius of the circle, and \( a \), \( b \), and \( c \) are the sides of the triangle.
Network Perimeter Check
In network management, a perimeter check involves ensuring the security of the network boundary. This is vital for protecting data and preventing unauthorized access. Key measures include:
- Implementing firewalls and intrusion detection systems
- Regularly updating security protocols
- Conducting vulnerability assessments
- Monitoring network traffic for suspicious activity
Importance of Perimeter Checks
Perimeter checks are crucial for maintaining the integrity and security of various systems, whether physical, mathematical, or digital. They help in early detection of potential issues, ensuring that corrective measures can be taken promptly to mitigate risks.
Conclusion
Whether in security, mathematics, or network management, a thorough perimeter check is essential for safeguarding against threats and ensuring smooth operations. Regular and systematic checks can prevent breaches and maintain the integrity of the protected area or system.

READ MORE:
Introduction to Perimeter Check
A perimeter check is a systematic inspection of the boundaries of an area, system, or network to ensure its security, integrity, and functionality. Perimeter checks are crucial in various fields such as physical security, mathematics, and network management. They help in identifying vulnerabilities, preventing unauthorized access, and maintaining the overall integrity of the area or system being protected.
Here are the key aspects of perimeter checks in different domains:
- Physical Security: Involves inspecting fences, walls, gates, and other physical barriers to ensure they are intact and secure.
- Mathematics: Refers to calculating the perimeter of geometric shapes to determine their boundary length.
- Network Management: Involves monitoring the network's edge to prevent unauthorized access and ensure data security.
Conducting a perimeter check typically involves the following steps:
- Planning: Define the scope and objectives of the perimeter check. Identify the boundaries and areas to be inspected.
- Inspection: Conduct a thorough examination of the perimeter. This includes visual inspections, using tools and technologies for detection, and checking for any signs of breaches or vulnerabilities.
- Analysis: Evaluate the findings from the inspection. Identify any weaknesses or areas that need improvement.
- Reporting: Document the results of the perimeter check. Provide recommendations for addressing any identified issues.
- Follow-up: Implement the recommended measures to enhance perimeter security. Schedule regular checks to ensure ongoing protection.
By following these steps, organizations can ensure their perimeters are secure and their systems are protected against potential threats.
Types of Perimeter Checks
Perimeter checks are essential for ensuring the security and integrity of various domains. Different types of perimeter checks cater to specific needs and applications. Here, we explore the primary types of perimeter checks in detail:
- Physical Security Perimeter Checks:
These checks involve inspecting the physical boundaries of a property or area to prevent unauthorized access and ensure safety. Key components include:
- Fences and Walls: Examining the condition and integrity of fences, walls, and other physical barriers.
- Gates and Entrances: Checking the security of gates, doors, and entry points for proper functioning and locking mechanisms.
- Surveillance Systems: Monitoring CCTV cameras and other surveillance equipment to ensure they are operational and covering the necessary areas.
- Security Patrols: Conducting regular patrols along the perimeter to detect and deter potential intrusions.
- Mathematical Perimeter Checks:
In mathematics, perimeter checks are used to calculate the boundary lengths of various geometric shapes. Key formulas include:
- Rectangle: \( P = 2(l + w) \)
- Square: \( P = 4s \)
- Circle: \( P = 2\pi r \)
- Triangle: \( P = a + b + c \)
These calculations help in various applications, such as land surveying, architecture, and design.
- Network Security Perimeter Checks:
These checks focus on securing the boundaries of a computer network to protect against cyber threats and unauthorized access. Essential components include:
- Firewalls: Implementing and monitoring firewalls to control incoming and outgoing network traffic based on predetermined security rules.
- Intrusion Detection Systems (IDS): Deploying IDS to detect and respond to potential security breaches.
- Vulnerability Scanning: Regularly scanning the network for vulnerabilities and addressing them promptly.
- Access Control: Ensuring that only authorized personnel have access to sensitive network areas and data.
Understanding the different types of perimeter checks and their specific applications helps in implementing effective security measures across various domains.
Physical Security Perimeter
Ensuring the security of a physical perimeter involves a comprehensive approach that includes multiple layers of defense. The objective is to prevent unauthorized access, detect intrusions, and respond promptly to any security breaches. Here are the key components and steps involved in securing a physical security perimeter:
Components of a Physical Security Perimeter
- Fences and Barriers:
Install and maintain fences, walls, and other physical barriers to delineate the perimeter. Ensure they are of adequate height and strength to deter intruders.
- Gates and Entry Points:
Secure all gates and entry points with robust locks, access control systems, and monitoring devices. Regularly check for functionality and signs of tampering.
- Surveillance Systems:
Deploy CCTV cameras and other surveillance equipment to cover all areas of the perimeter. Ensure cameras are positioned to eliminate blind spots and are functioning correctly.
- Lighting:
Implement adequate lighting along the perimeter to enhance visibility and deter potential intruders. Motion-activated lights can provide an additional layer of security.
- Signage:
Install clear and visible signage indicating that the area is under surveillance and unauthorized access is prohibited. This can serve as a deterrent to potential intruders.
- Security Patrols:
Conduct regular patrols by security personnel along the perimeter. Vary patrol routes and schedules to prevent predictability and enhance detection capabilities.
Steps to Secure a Physical Security Perimeter
- Assessment and Planning:
Conduct a thorough assessment of the current perimeter security measures. Identify vulnerabilities and areas that need improvement. Develop a comprehensive security plan addressing all identified issues.
- Installation and Upgrades:
Install necessary security infrastructure, including fences, gates, surveillance systems, and lighting. Upgrade existing measures to meet current security standards.
- Routine Inspections:
Regularly inspect all physical security components for signs of wear, damage, or tampering. Ensure that all systems are functioning correctly and address any issues promptly.
- Monitoring and Surveillance:
Continuously monitor the perimeter using surveillance systems. Ensure that all footage is recorded and reviewed for any suspicious activity.
- Response Protocols:
Establish clear protocols for responding to security breaches. Train security personnel on these protocols to ensure a quick and effective response.
- Regular Training:
Provide ongoing training for security personnel to keep them updated on the latest security practices and technologies. Conduct regular drills to ensure preparedness for various scenarios.
By implementing these components and following these steps, organizations can establish a robust physical security perimeter that effectively protects their assets and personnel from unauthorized access and potential threats.
Electronic Security Measures
Electronic security measures are critical components of modern perimeter security systems. These measures leverage advanced technology to detect, monitor, and respond to potential threats. Here are the key electronic security measures used to enhance perimeter security:
Components of Electronic Security Measures
- Surveillance Cameras:
Install CCTV cameras strategically around the perimeter to provide continuous monitoring. Ensure cameras have night vision capabilities and cover all potential entry points and blind spots.
- Motion Detectors:
Deploy motion sensors to detect movement along the perimeter. These sensors can trigger alarms or activate cameras to capture real-time footage of intrusions.
- Access Control Systems:
Implement electronic access control systems at all entry points. These systems can include keycards, biometric scanners, or PIN codes to restrict access to authorized personnel only.
- Alarm Systems:
Install alarm systems that are connected to motion detectors, door and window sensors, and other intrusion detection devices. Alarms can be configured to alert security personnel or trigger automatic responses.
- Perimeter Intrusion Detection Systems (PIDS):
Use PIDS to detect and alert on any attempts to breach the perimeter barriers. These systems often include a combination of sensors, including infrared, microwave, and vibration sensors.
- Lighting Controls:
Integrate lighting controls with motion detectors to illuminate areas where movement is detected. This enhances visibility and acts as a deterrent to intruders.
Steps to Implement Electronic Security Measures
- Assessment and Planning:
Conduct a thorough assessment of the perimeter to identify vulnerable areas and determine the appropriate electronic security measures. Develop a detailed plan outlining the placement and integration of these measures.
- Installation:
Install the electronic security components according to the plan. Ensure all devices are properly configured and integrated with the overall security system.
- Testing:
Test all electronic security devices to ensure they are functioning correctly. Simulate various intrusion scenarios to verify the effectiveness of the system.
- Monitoring:
Establish a central monitoring station to oversee the electronic security measures. Ensure that surveillance footage and sensor alerts are continuously monitored for any signs of intrusion.
- Maintenance:
Perform regular maintenance on all electronic security devices. This includes updating software, replacing batteries, and repairing or replacing faulty equipment.
- Training:
Train security personnel on how to use and monitor the electronic security systems effectively. Conduct regular drills to ensure readiness in responding to security breaches.
By implementing these electronic security measures, organizations can significantly enhance their perimeter security, ensuring a robust defense against potential intrusions and threats.

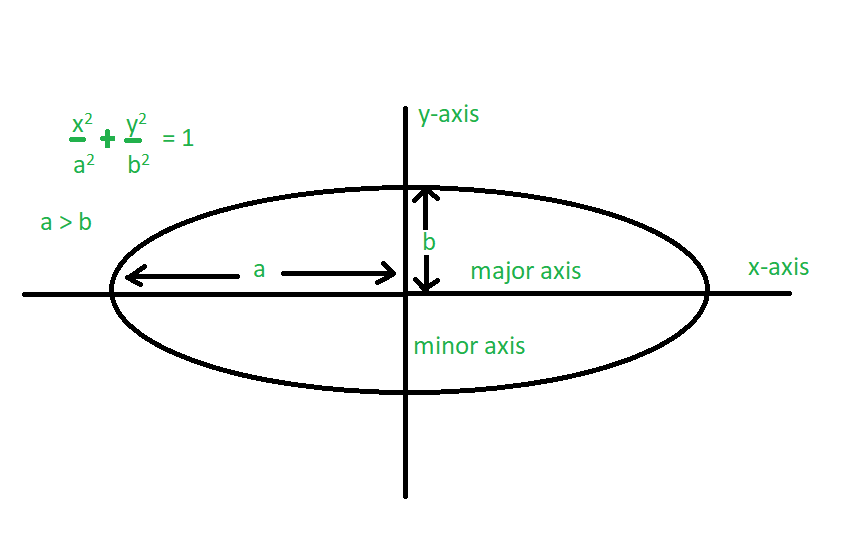
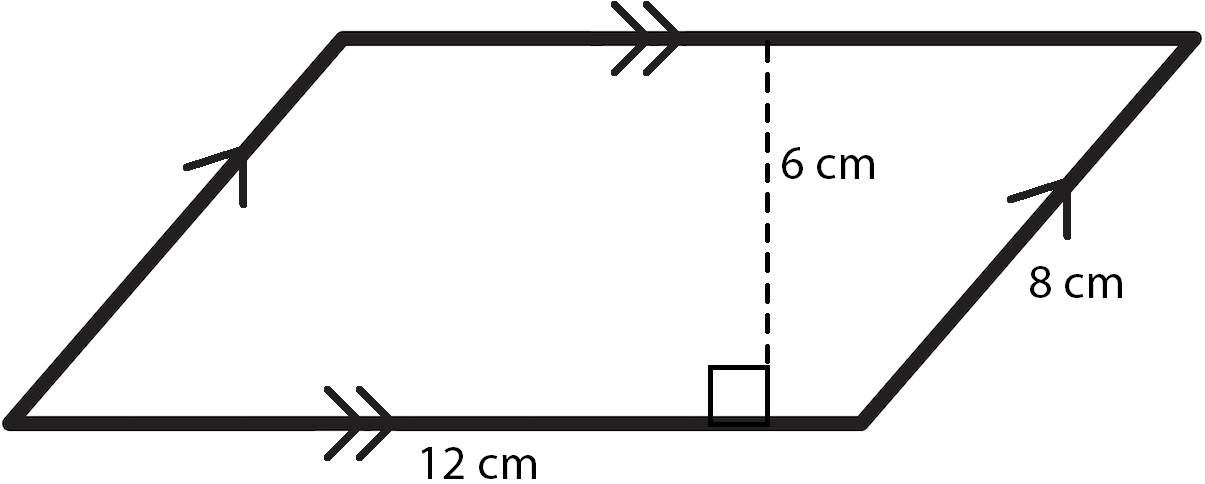
Geometric Shapes and Perimeter Calculation
Calculating the perimeter of geometric shapes is a fundamental concept in geometry, essential for various practical applications. This section explores the perimeter calculations for common geometric shapes, providing detailed steps and formulas.
Common Geometric Shapes and Their Perimeter Formulas
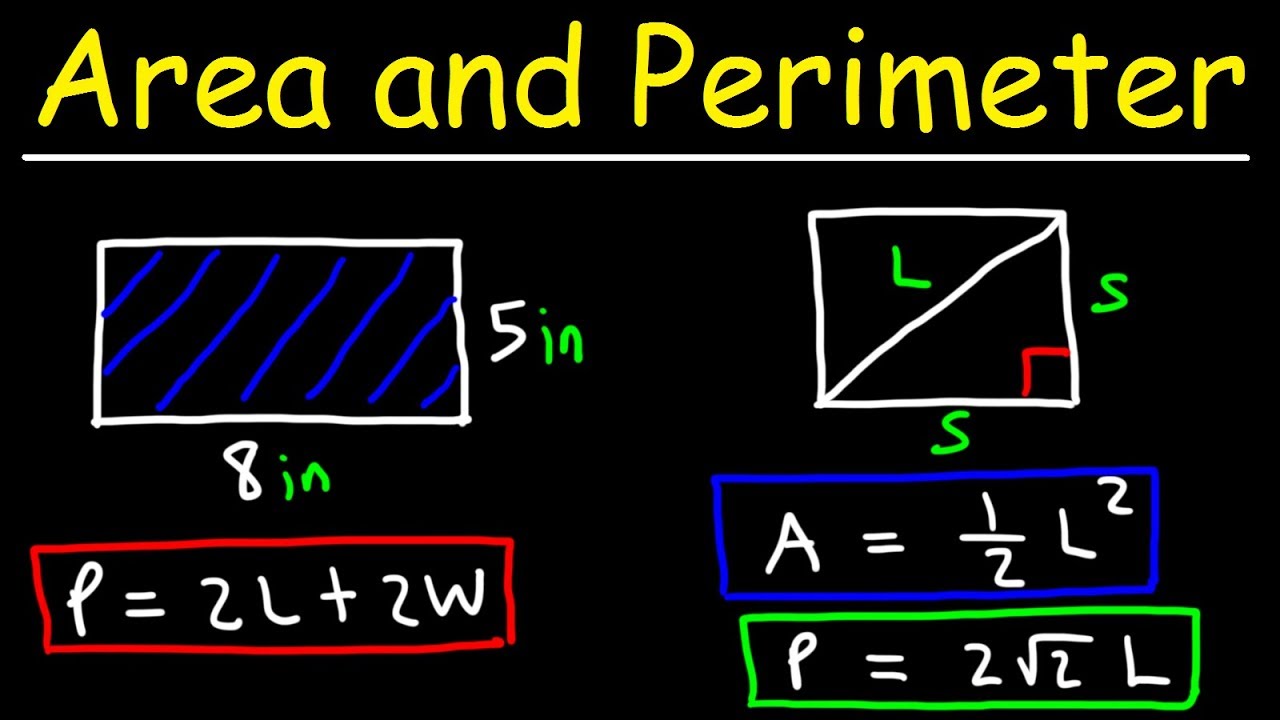
- Rectangle:
To find the perimeter \( P \) of a rectangle, use the formula:
\[ P = 2(l + w) \]
where \( l \) is the length and \( w \) is the width.
- Square:
The perimeter \( P \) of a square is calculated by:
\[ P = 4s \]
where \( s \) is the length of one side.
- Circle:
The perimeter (circumference) \( C \) of a circle is given by:
\[ C = 2\pi r \]
where \( r \) is the radius of the circle.
- Triangle:
The perimeter \( P \) of a triangle is the sum of its sides:
\[ P = a + b + c \]
where \( a \), \( b \), and \( c \) are the lengths of the triangle's sides.
- Polygon:
For a polygon with \( n \) sides, the perimeter \( P \) is calculated as:
\[ P = \sum_{i=1}^{n} s_i \]
where \( s_i \) are the lengths of the sides.
Steps to Calculate Perimeters
- Identify the Shape:
Determine the geometric shape for which you need to calculate the perimeter. This is crucial for selecting the appropriate formula.
- Measure Dimensions:
Accurately measure the necessary dimensions, such as side lengths, radius, or diameter. Use appropriate tools like rulers, measuring tapes, or calipers.
- Apply the Formula:
Use the corresponding perimeter formula for the identified shape. Substitute the measured dimensions into the formula to calculate the perimeter.
- Verify Results:
Double-check your measurements and calculations to ensure accuracy. Correct any discrepancies to avoid errors in the final result.
Examples of Perimeter Calculation
- Example 1:
Calculate the perimeter of a rectangle with a length of 10 units and a width of 5 units.
\[ P = 2(10 + 5) = 2 \times 15 = 30 \text{ units} \]
- Example 2:
Find the perimeter of a square with a side length of 7 units.
\[ P = 4 \times 7 = 28 \text{ units} \]
- Example 3:
Determine the circumference of a circle with a radius of 3 units.
\[ C = 2\pi \times 3 \approx 18.85 \text{ units} \]
- Example 4:
Calculate the perimeter of a triangle with side lengths of 3 units, 4 units, and 5 units.
\[ P = 3 + 4 + 5 = 12 \text{ units} \]
Understanding how to calculate the perimeter of geometric shapes is essential for various applications, including construction, design, and education. Mastery of these calculations ensures precision and efficiency in practical tasks.
Real-world Applications of Perimeter in Math
Understanding the perimeter of various shapes is crucial in a wide array of real-world scenarios. Below are detailed applications where perimeter calculations are essential:
-
Fencing and Landscaping
When building a fence around a garden or property, calculating the perimeter ensures that the correct amount of fencing material is purchased. For example, a rectangular garden with a length of 20 feet and a width of 30 feet would require a fence with a perimeter of:
\[ P = 2 \times (20 \, \text{ft} + 30 \, \text{ft}) = 100 \, \text{ft} \]
This calculation helps in planning the fencing materials needed.
-
Construction Projects
In construction, knowing the perimeter of a plot or a building area helps in determining the amount of materials needed for foundations, walls, and other structures. For instance, constructing a rectangular shed with dimensions 10 feet by 12 feet would require perimeter calculations for framing:
\[ P = 2 \times (10 \, \text{ft} + 12 \, \text{ft}) = 44 \, \text{ft} \]
-
Interior Design
When installing moldings or baseboards in a room, the perimeter is used to measure the total length needed. For example, if a room is 15 feet by 18 feet, the perimeter is:
\[ P = 2 \times (15 \, \text{ft} + 18 \, \text{ft}) = 66 \, \text{ft} \]
This ensures the correct amount of material is purchased for the project.
-
Surveying and Land Measurement
Surveyors use perimeter to measure land plots. This is critical for defining property boundaries and planning the layout of new developments. For example, a pentagonal plot with sides measuring 50 feet each has a perimeter of:
\[ P = 5 \times 50 \, \text{ft} = 250 \, \text{ft} \]
-
Sports and Recreation
In sports field design, such as a soccer field, calculating the perimeter helps in planning boundary lines and tracks. A standard soccer field of 100 meters by 64 meters has a perimeter of:
\[ P = 2 \times (100 \, \text{m} + 64 \, \text{m}) = 328 \, \text{m} \]
-
Gardening
When creating garden beds or pathways, the perimeter measurement helps determine the amount of edging or border material required. For a rectangular flower bed measuring 8 feet by 5 feet, the perimeter is:
\[ P = 2 \times (8 \, \text{ft} + 5 \, \text{ft}) = 26 \, \text{ft} \]
-
Painting and Wallpapering
For painting or wallpapering a room, the perimeter helps calculate the length of borders or decorative strips needed. If a room is 12 feet by 10 feet, the perimeter would be:
\[ P = 2 \times (12 \, \text{ft} + 10 \, \text{ft}) = 44 \, \text{ft} \]
These examples illustrate how perimeter calculations are vital in various fields, providing the necessary information to plan and execute projects efficiently.
Network Security Basics
Network security involves the measures taken to protect the integrity, confidentiality, and accessibility of computer networks and data using both hardware and software technologies. It encompasses a variety of strategies and tools designed to safeguard the network from cyberattacks, data breaches, and other security threats.
Common Network Security Risks
- Unauthorized Access: Gaining access to a network without permission, potentially viewing or leaking confidential information.
- DDoS Attacks: Distributed Denial-of-Service attacks aim to disrupt network services by overwhelming them with traffic.
- Vulnerability Exploits: Attackers use weaknesses in software, hardware, or login portals to gain unauthorized access.
- Malware Infections: Malicious software such as viruses, ransomware, and spyware that can damage or steal data.
- Insider Threats: Security risks posed by employees or contractors who may intentionally or unintentionally compromise network security.
Essential Network Security Technologies
- Firewalls: Hardware or software solutions that filter incoming and outgoing traffic based on predetermined security rules.
- Virtual Private Networks (VPNs): Securely encrypts connections from remote users to the network, protecting data transmitted over public networks.
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS): Monitor network traffic for suspicious activity and take action to prevent potential threats.
- Anti-virus and Anti-malware Software: Protects against malicious software by detecting, quarantining, and removing malware.
- Network Access Control (NAC): Restricts access to the network based on policies, ensuring only authorized users and devices can connect.
- Data Loss Prevention (DLP): Prevents sensitive data from being transmitted outside the network by monitoring and controlling data flows.
- Web Application Firewalls (WAF): Protects web applications by filtering and monitoring HTTP traffic between a web application and the internet.
Steps to Enhance Network Security
- Implement Strong Access Controls: Use multi-factor authentication and enforce strong password policies to ensure that only authorized users can access the network.
- Regular Software and Hardware Updates: Keep all systems updated with the latest security patches to protect against known vulnerabilities.
- Network Segmentation: Divide the network into smaller segments to limit the spread of an attack and improve traffic management.
- Conduct Regular Security Audits: Regularly review and assess network security measures to identify and address potential weaknesses.
- Employee Training: Educate employees about cybersecurity best practices and how to recognize potential threats such as phishing attacks.
Firewalls and Intrusion Detection Systems
Firewalls and Intrusion Detection Systems (IDS) are crucial components of network security, each serving distinct roles in protecting an organization's digital assets. Below is a comprehensive guide on their functionalities, types, and deployment strategies.
Firewalls
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between a trusted internal network and untrusted external networks such as the internet.
- Types of Firewalls:
- Network-based Firewalls: These are deployed at the network perimeter and filter traffic to and from the network.
- Host-based Firewalls: Installed on individual devices to protect them from threats specific to that host.
- Classification of Firewalls:
- Hardware Firewalls: Dedicated devices that provide a robust solution for network security.
- Software Firewalls: Programs installed on computers and devices to filter traffic.
- Packet-filter Firewalls: Examine packets and allow or deny based on rules.
- Proxy Firewalls: Intercept all messages entering and leaving the network.
- Application Gateways: Apply security mechanisms to specific applications, such as FTP and Telnet servers.
- Circuit-level Gateways: Monitor TCP handshaking and session initiation.
- Stateful Packet Inspection (SPI): Track the state of active connections and make decisions based on the context of the traffic.
Intrusion Detection Systems (IDS)
An IDS monitors network traffic for suspicious activity and alerts administrators about potential threats. Unlike firewalls, IDS are passive systems that do not block traffic but analyze it.
- Types of IDS:
- Network Intrusion Detection Systems (NIDS): Monitor traffic at strategic points in the network, often at the perimeter.
- Host Intrusion Detection Systems (HIDS): Monitor the activity on individual devices, capturing logins, file accesses, and changes.
- Protocol-based IDS (PIDS): Monitor the protocols used for communication between servers and devices.
- Application Protocol-based IDS (APIDS): Monitor the application layer protocols, often used between web servers and databases.
- Hybrid IDS: Combine multiple IDS types for comprehensive security coverage.
- Detection Methods:
- Signature-based Detection: Compares network traffic to known attack patterns or signatures.
- Anomaly-based Detection: Establishes a baseline of normal activity and flags deviations from this baseline as potential threats.
Intrusion Prevention Systems (IPS)
Similar to IDS, Intrusion Prevention Systems (IPS) monitor network traffic for suspicious activities but also take active steps to prevent threats, such as blocking malicious traffic in real time.
- Key Functions of IPS:
- Monitoring and analyzing network traffic.
- Performing deep packet inspection.
- Using signature-based and anomaly-based detection methods.
- Blocking or rerouting malicious traffic.
- Alerting administrators to suspicious activities.
Firewalls and IDS/IPS form a layered defense strategy that significantly enhances the security posture of an organization. By implementing these tools effectively, organizations can better protect their networks from a wide array of cyber threats.

Vulnerability Assessments
Vulnerability assessments are essential for identifying, quantifying, and prioritizing the security weaknesses in an organization's IT environment. This process helps in protecting against data breaches and ensuring compliance with regulations such as GDPR and PCI DSS.
Steps for Conducting a Vulnerability Assessment
-
Program Scoping and Preparation
Define the scope and goals of the vulnerability assessment. Identify all assets, equipment, and endpoints to be included in the scan, along with the corresponding security controls and policies. -
Vulnerability Testing
Conduct automated scans using tools to identify potential vulnerabilities. This phase leverages databases and threat intelligence feeds to detect and classify vulnerabilities. -
Prioritization
Review and prioritize vulnerabilities based on risk factors such as the severity of the vulnerability, the impact on the organization, the likelihood of exploitation, and the availability of patches. -
Reporting
Generate comprehensive reports that detail the vulnerabilities discovered, their impact, and remediation steps. This helps the security team understand and address the issues effectively. -
Continuous Improvement
Conduct regular and frequent assessments to detect new vulnerabilities as they arise and ensure previously identified vulnerabilities are effectively resolved.
Types of Vulnerability Assessments
-
Network-based Scan
Identifies vulnerabilities in network security, including traditional and wireless networks. Ensures enforcement of existing network security controls and policies. -
Host-based Scan
Identifies vulnerabilities in systems, servers, containers, workstations, and other network hosts. Provides visibility into system configuration and patch history. -
Application Scan
Identifies vulnerabilities in software applications, including architecture, source code, and database misconfigurations. -
Database Scan
Identifies vulnerabilities within database systems or servers, helping prevent attacks such as SQL injections.
Popular Vulnerability Assessment Tools
-
OpenVAS
An open-source vulnerability assessment tool known for its adaptability and extensive reporting options. It is resource-intensive and may generate false positives. -
Tenable.io
A cloud-based platform that offers real-time monitoring and a wide range of scanning options. It integrates with third-party tools but can be expensive and complex for larger organizations. -
Invicti
Formerly known as Netsparker, this tool specializes in web application vulnerability scanning and offers thorough reporting and ongoing monitoring. It is user-friendly but can be costly.
Benefits of Vulnerability Assessments
- Improves IT security by identifying and addressing vulnerabilities before they can be exploited.
- Saves time and resources through automated scanning and reporting.
- Enhances consumer trust and prevents negative publicity from data breaches.
- Helps achieve compliance with data privacy laws and other regulations.
Vulnerability Testing Methods
-
Active Testing
Involves direct interaction with the target system to identify security weaknesses. It is intrusive but effective in finding vulnerabilities. -
Passive Testing
Observes and analyzes the target system without direct interaction. It is less disruptive but may miss some vulnerabilities.
Steps for Conducting a Perimeter Check
Conducting a perimeter check involves several crucial steps to ensure the security and integrity of a given area. These steps include planning, execution, and review phases. Below are detailed steps for each phase:
Planning and Preparation
- Identify Objectives: Determine the goals of the perimeter check, such as identifying vulnerabilities or ensuring compliance with security protocols.
- Gather Resources: Collect necessary tools, personnel, and documents required for the perimeter check.
- Site Evaluation: Conduct a thorough assessment of the perimeter, noting all entry points, barriers, and existing security measures.
- Develop a Checklist: Create a comprehensive checklist to guide the inspection process, ensuring all aspects of the perimeter are evaluated.
Execution and Monitoring
- Physical Inspection: Walk the perimeter to visually inspect fences, gates, and other physical barriers. Ensure there are no breaches, damage, or weak points.
- Access Control Systems: Test the functionality of access control measures such as locks, key card systems, and biometric scanners.
- Detection Systems: Evaluate the effectiveness of detection systems like CCTV cameras, motion sensors, and alarm systems. Ensure they cover all critical areas and are in good working condition.
- Environmental Controls: Check environmental controls in sensitive areas, such as temperature and humidity in server rooms, to ensure they are functioning correctly.
- Documentation: Record findings during the inspection, noting any issues or areas needing improvement.
Review and Analysis
- Analyze Findings: Review the inspection data to identify vulnerabilities, security gaps, and areas for improvement.
- Report Generation: Create a detailed report outlining the findings, including photographs and documentation of identified issues.
- Recommendation Development: Provide actionable recommendations to address any identified vulnerabilities or weaknesses.
- Follow-Up Actions: Implement recommended security measures and schedule regular follow-up inspections to ensure ongoing perimeter integrity.
By following these steps, organizations can systematically evaluate and enhance the security of their perimeters, thereby reducing the risk of unauthorized access and other security threats.
Planning and Preparation
Effective planning and preparation are crucial steps in conducting a successful perimeter check. This process ensures that all potential vulnerabilities are identified and addressed systematically. Here are the detailed steps for planning and preparation:
-
Define Objectives and Scope
Clearly outline the objectives of the perimeter check. Determine the scope by identifying the areas and assets that need to be protected. This step helps in understanding the requirements and constraints of the security check.
-
Risk Assessment
Conduct a comprehensive risk assessment to identify potential threats and vulnerabilities. Evaluate the likelihood and impact of different security risks. Use this information to prioritize areas that need immediate attention.
-
Resource Allocation
Allocate necessary resources, including personnel, tools, and technologies, required for the perimeter check. Ensure that all team members are adequately trained and equipped to handle their tasks effectively.
-
Develop a Checklist
Create a detailed checklist of all the tasks that need to be performed during the perimeter check. This list should include physical inspections, electronic monitoring, and verification of security measures.
-
Establish Communication Protocols
Set up clear communication protocols to ensure smooth coordination among team members. Use secure communication channels to prevent any unauthorized access to sensitive information.
-
Scheduling
Schedule the perimeter check at a time that minimizes disruption to normal operations. Ensure that the schedule allows for thorough inspections without compromising security.
-
Documentation
Prepare all necessary documentation, including maps, floor plans, and security policies. Documenting the current security measures helps in identifying gaps and areas for improvement.
-
Briefing and Training
Conduct a briefing session for all team members involved in the perimeter check. Provide training on the use of equipment and procedures to be followed during the inspection.
By following these steps, organizations can ensure that their perimeter checks are thorough, systematic, and effective in identifying and mitigating security risks.
Execution and Monitoring
Execution and monitoring of perimeter checks are critical components in maintaining security and ensuring the integrity of a site or system. This process involves several key steps and the implementation of various tools and technologies to achieve effective monitoring and prompt response to any breaches or anomalies.
-
Initial Setup and Configuration
- Install and configure perimeter security cameras strategically to cover all vulnerable areas. Ensure these cameras can operate in various light conditions and have capabilities like thermal imaging for low-light environments.
- Set up perimeter lighting and motion sensors to enhance visibility and detect movement around the perimeter. Use motion sensor lights to deter potential intruders by spotlighting them when they approach.
- Deploy access control systems at all entry points to manage and monitor who enters and exits the premises. This system should integrate with a database to verify credentials and log access events.
-
Real-time Monitoring
- Utilize video monitoring systems to provide continuous surveillance. Ensure that cameras are monitored by trained personnel or automated systems capable of detecting and analyzing suspicious activity.
- Implement an intrusion detection system (IDS) to alert security personnel of any unauthorized access attempts. IDS can include physical sensors on fences or gates and software-based monitoring for network perimeters.
- Employ integrated security management software to centralize monitoring and control. This software can provide real-time alerts, incident logging, and detailed reports for security audits.
-
Response and Incident Management
- Establish a protocol for responding to security alerts. This should include immediate verification of the threat, appropriate action (e.g., dispatching security personnel, locking down areas), and communication with law enforcement if necessary.
- Use automated systems to issue warnings or alerts to intruders through audio speakers connected to the monitoring system. This can deter intruders before they cause harm or gain access.
- Regularly update and patch security systems to protect against new vulnerabilities. Cyber hardening techniques should be employed to prevent malware from compromising the perimeter security infrastructure.
-
Review and Optimization
- Conduct regular audits and reviews of the security systems and protocols to identify weaknesses and areas for improvement. Use data from security logs and incident reports to inform these reviews.
- Optimize systems to reduce false alarms and ensure that genuine threats are promptly identified and addressed. This can involve adjusting sensor sensitivity, refining access control parameters, and enhancing the integration between different security components.
- Train security personnel continuously on the latest security protocols, technologies, and response strategies to ensure they are prepared to handle various security scenarios effectively.
Effective execution and monitoring of perimeter checks are essential for maintaining robust security. By utilizing a combination of advanced technologies and well-defined protocols, organizations can safeguard their perimeters against unauthorized access and potential threats.

Review and Analysis
Reviewing and analyzing the results of a perimeter check is a critical step to ensure that the security measures are effective and that any vulnerabilities are identified and addressed. This section outlines a comprehensive approach to review and analysis, covering the key steps and considerations.
Steps for Review and Analysis
-
Data Collection
- Gather logs and reports from all perimeter security tools, including firewalls, IDS/IPS, and UTM systems.
- Collect network traffic data and alerts generated during the perimeter check.
-
Data Analysis
- Analyze log files for any unusual or suspicious activities.
- Identify patterns or repeated attempts of breaches.
- Utilize data visualization tools to map out attack vectors and points of failure.
-
Risk Assessment
- Evaluate the severity and impact of identified vulnerabilities.
- Determine the potential risk to critical assets and operations.
-
Policy and Procedure Review
- Review current security policies and procedures for any gaps or weaknesses.
- Ensure policies are up-to-date with the latest security standards and best practices.
-
Report Generation
- Create a detailed report summarizing the findings, including identified vulnerabilities, risks, and recommended actions.
- Include visual aids such as charts and graphs to illustrate key points.
Key Considerations
-
Continuous Monitoring
Implement continuous monitoring practices to ensure ongoing security and to quickly identify new threats. Utilize automated tools and AI-driven solutions to enhance real-time threat detection and response.
-
Regular Audits
Conduct regular security audits to reassess the perimeter security posture and make necessary adjustments. Regular audits help in identifying any lapses and ensuring compliance with security policies.
-
Incident Response Plan
Develop and maintain an incident response plan to address potential security breaches promptly and effectively. Ensure that the plan includes clear roles and responsibilities, communication protocols, and recovery procedures.
Tools for Review and Analysis
Several tools can aid in the review and analysis process:
- SIEM (Security Information and Event Management) Systems: These tools aggregate and analyze log data from various security devices, providing comprehensive insights into security events.
- Network Analyzers: Tools like Wireshark help in capturing and analyzing network traffic to detect anomalies and potential threats.
- Vulnerability Scanners: Tools such as Nessus or OpenVAS scan the network for known vulnerabilities and provide detailed reports on security weaknesses.
By following these steps and utilizing the appropriate tools, organizations can ensure a thorough review and analysis of their perimeter checks, thereby enhancing their overall security posture.
Tools and Technologies for Perimeter Checks
Effective perimeter checks require a combination of tools and technologies tailored to the specific needs of the area being secured. Here are some of the key tools and technologies used in various types of perimeter checks:
Security Tools
- Surveillance Cameras: Modern security cameras, including high-resolution and thermal cameras, provide continuous monitoring and recording of the perimeter. AI-enabled cameras enhance detection capabilities by analyzing video feeds in real-time to identify suspicious activities.
- Intrusion Detection Systems (IDS): These systems monitor network traffic for suspicious activities and send alerts to security personnel when potential threats are detected.
- Intrusion Prevention Systems (IPS): Building on IDS, IPS not only detects but also prevents threats by taking proactive measures to block malicious activities.
- Physical Barriers: Fences, walls, and gates serve as the first line of defense by physically blocking unauthorized access.
- Access Control Systems: These systems regulate who can enter and exit the premises, using key cards, biometric scanners, and other authentication methods.
- Perimeter Lighting: Adequate lighting enhances visibility around the perimeter, deterring intruders and improving camera performance.
- Perimeter Intrusion Detection Systems (PIDS): These include sensors that detect movement, vibration, and other disturbances, triggering alarms when unauthorized access is attempted.
Mathematical Tools
- Geometric Calculations: Tools for calculating the perimeter of geometric shapes are essential for planning and verifying physical security measures.
- Software Applications: Various software tools can assist in perimeter calculations, providing accurate measurements and visual representations for better planning.
Network Security Tools
- Firewalls: These are essential for controlling the flow of traffic between trusted internal networks and untrusted external networks, blocking unauthorized access while permitting legitimate communication.
- Unified Threat Management (UTM) Systems: UTM systems integrate multiple security functions, such as firewall, IDS/IPS, antivirus, and VPN, into a single platform, simplifying management and enhancing security.
- Border Routers: Positioned at the network edge, these routers manage traffic flow between the internal network and the internet, ensuring only legitimate traffic is allowed.
- AI and Machine Learning: Advanced AI-driven solutions improve real-time threat detection and response, analyzing data to identify and mitigate potential security threats.
- Cloud Security Solutions: As more organizations move to cloud environments, specialized tools are necessary to secure cloud perimeters, protecting data and applications from cyber threats.
By integrating these tools and technologies, organizations can create a robust and multi-layered perimeter security system that effectively detects, deters, and responds to various types of intrusions and threats.
Security Tools
Ensuring a robust perimeter security system involves leveraging various tools and technologies. These tools help detect, delay, and respond to potential intrusions effectively. Here are some key security tools commonly used in perimeter checks:
-
Physical Barriers:
These include walls, fences, and gates that define the boundaries of a property. Physical barriers act as the first line of defense, deterring unauthorized access.
-
Surveillance Cameras:
Closed-circuit television (CCTV) systems allow continuous monitoring of the perimeter. Modern surveillance cameras offer high-resolution video, night vision, and remote monitoring capabilities.
-
Access Control Systems:
These systems regulate and monitor who can enter the premises. Technologies such as key cards, biometric scanners, and RFID readers ensure that only authorized individuals gain access.
-
Perimeter Intrusion Detection Systems (PIDS):
PIDS utilize sensors to detect unauthorized breaches. Examples include motion detectors, glass-break sensors, and perimeter alarms.
-
AI-enabled Technologies:
Integrating AI with existing cameras and sensors enables 24/7 continuous monitoring, precise detection of intruders, and real-time alerts to security personnel.
-
Firewalls:
Firewalls act as a barrier between your internal network and external threats, allowing or blocking traffic based on a defined set of security rules.
-
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS):
IDS monitor network traffic for suspicious activity and alert administrators. IPS, on the other hand, not only detect but also attempt to prevent threats automatically.
Combining these tools creates a layered security approach, where each layer complements and reinforces the others, providing comprehensive protection against intrusions.
Mathematical Tools
Mathematical tools for perimeter checks are essential for accurately calculating the perimeter of various geometric shapes. These tools include formulas, software, and instruments that aid in the precise measurement and computation of perimeters in different contexts.
Formulas for Common Shapes
- Square: The perimeter \( P \) of a square with side length \( a \) is given by \( P = 4a \).
- Rectangle: The perimeter \( P \) of a rectangle with length \( l \) and width \( w \) is \( P = 2(l + w) \).
- Circle: The perimeter, or circumference \( C \), of a circle with radius \( r \) is \( C = 2\pi r \).
- Triangle: The perimeter \( P \) of a triangle with sides \( a \), \( b \), and \( c \) is \( P = a + b + c \).
- Regular Polygon: For a regular polygon with \( n \) sides of length \( a \), the perimeter \( P \) is \( P = n \cdot a \).
Software and Online Tools
Various software and online tools can assist in calculating perimeters. These tools often provide visual aids and step-by-step solutions, making it easier to understand and verify calculations.
- Geogebra: A dynamic mathematics software that supports geometry, algebra, and calculus, useful for visualizing and calculating perimeters.
- Wolfram Alpha: An online computational engine that can solve complex perimeter problems and provide detailed explanations.
- Desmos: An advanced graphing calculator that can help visualize and compute perimeters for various geometric shapes.
Instruments for Measurement
In practical scenarios, especially in fields like construction and land surveying, physical instruments are crucial for measuring perimeters accurately:
- Measuring Tape: A flexible ruler used to measure the length of the sides of various objects and spaces.
- Laser Distance Meter: A device that uses a laser beam to measure the distance between two points, useful for large-scale perimeter measurements.
- Protractor and Ruler: Basic tools for measuring and drawing precise lengths and angles, essential for geometric calculations.
Applications of Perimeter Calculation
Understanding and calculating perimeters is vital in numerous real-world applications:
- Architecture and Construction: Accurate perimeter measurements are essential for planning layouts, constructing buildings, and ensuring structural integrity.
- Landscaping: Perimeter calculations help in designing gardens, parks, and outdoor spaces by determining the boundaries and required materials.
- Sports: Perimeters of fields and tracks are measured to adhere to regulations and optimize space utilization.
Examples
- Rectangle: For a rectangle with length 7 units and width 4 units, the perimeter \( P \) is \( P = 2(7 + 4) = 22 \) units.
- Circle: For a circle with radius 7 feet, the perimeter (circumference) \( C \) is \( C = 2\pi \cdot 7 = 44 \) feet.
- Square: For a square with side length 4 meters, the perimeter \( P \) is \( P = 4 \cdot 4 = 16 \) meters.
Network Security Tools
Network security tools are essential for protecting your organization's IT infrastructure from various cyber threats. Here are some of the key network security tools used to safeguard networks:
-
Firewalls
Firewalls are the first line of defense in network security. They monitor incoming and outgoing traffic and decide whether to allow or block specific traffic based on predetermined security rules. Modern firewalls, such as Next-Generation Firewalls (NGFWs), offer advanced features like application awareness and control, integrated intrusion prevention, and cloud-delivered threat intelligence.
-
Intrusion Detection and Prevention Systems (IDPS)
IDPS tools monitor network traffic for suspicious activity and known threats. They can detect and prevent potential attacks by analyzing the network traffic and comparing it against a database of known threat signatures. These systems can operate in detection mode (alerting administrators of potential threats) or prevention mode (blocking the malicious activity).
-
Security Information and Event Management (SIEM)
SIEM solutions collect and analyze log data from various sources within the network, providing real-time analysis of security alerts. SIEM tools help organizations detect and respond to security incidents more efficiently by correlating events from different systems and generating actionable insights. Popular SIEM tools include Splunk, IBM QRadar, and SolarWinds Security Event Manager.
-
Endpoint Detection and Response (EDR)
EDR tools focus on monitoring and protecting endpoints such as desktops, laptops, and mobile devices. They provide visibility into endpoint activities, detect suspicious behavior, and enable rapid response to threats. EDR solutions often include features like threat hunting, automated response actions, and incident investigation capabilities.
-
Vulnerability Scanners
Vulnerability scanners, such as Nessus and Qualys, are used to identify security weaknesses in network devices, applications, and systems. These tools perform regular scans to detect vulnerabilities that could be exploited by attackers. They provide detailed reports and recommendations for remediation, helping organizations to proactively address potential security gaps.
-
Network Access Control (NAC)
NAC solutions enforce security policies on devices accessing the network. They ensure that only authorized and compliant devices can connect to the network, reducing the risk of unauthorized access. NAC tools often include features like device profiling, guest access management, and endpoint compliance checks.
-
Unified Threat Management (UTM)
UTM solutions integrate multiple security functions into a single platform, providing comprehensive protection against a wide range of threats. UTM tools typically include firewall, intrusion prevention, anti-virus, anti-spam, VPN, and web content filtering capabilities. This all-in-one approach simplifies security management and reduces costs.
-
Advanced Threat Protection (ATP)
ATP solutions are designed to protect against sophisticated threats, such as zero-day exploits and advanced persistent threats (APTs). These tools use techniques like sandboxing, machine learning, and behavioral analysis to detect and mitigate advanced threats that traditional security measures might miss.
Implementing a combination of these network security tools helps organizations create a robust security posture, capable of defending against a diverse array of cyber threats.
Best Practices for Effective Perimeter Checks
Conducting effective perimeter checks is essential to maintaining robust security for any organization. Here are some best practices to ensure your perimeter checks are thorough and effective:
1. Regular Inspections
Regular inspections are crucial to identify any vulnerabilities or breaches in the perimeter. This includes both physical and digital checks:
- Physical Inspections: Regularly walk the perimeter to check for any signs of tampering, damage, or unauthorized access points.
- Digital Inspections: Use automated tools to scan for network vulnerabilities and ensure firewall and security systems are functioning properly.
2. Updating Security Measures
Security threats are constantly evolving, so it's important to keep your security measures up-to-date:
- Software Updates: Regularly update firewalls, antivirus software, and intrusion detection systems to protect against new threats.
- Hardware Upgrades: Replace outdated security equipment with newer, more effective technology as it becomes available.
3. Training and Awareness
Training staff and raising awareness about security practices can greatly enhance perimeter security:
- Employee Training: Provide regular training sessions on security protocols and emergency response procedures.
- Security Drills: Conduct regular security drills to ensure everyone knows how to respond in the event of a security breach.
4. Integration of Advanced Technologies
Incorporate advanced technologies to strengthen perimeter security:
- Thermal Imaging: Use thermal cameras to detect intruders even in low visibility conditions.
- Video Analytics: Implement video analytics to automatically identify and alert on suspicious activities.
- Automated Response Systems: Set up automated systems to trigger alarms, lock doors, or notify security personnel when a breach is detected.
5. Collaboration and Communication
Ensure effective communication and collaboration between different teams responsible for security:
- Security and Operations Teams: Maintain close collaboration between security and operations staff to ensure seamless integration of security measures with daily operations.
- Incident Response Teams: Establish clear communication channels and protocols for incident response teams to quickly address any security breaches.
6. Continuous Monitoring and Improvement
Continuously monitor and improve your perimeter security measures:
- Monitoring Systems: Use advanced monitoring systems to continuously track and analyze perimeter security data.
- Feedback and Improvement: Regularly review security performance and incorporate feedback to improve security measures.
7. Policy and Procedure Management
Maintain and enforce strong security policies and procedures:
- Access Control Policies: Define and enforce strict access control policies to prevent unauthorized access.
- Regular Audits: Conduct regular audits of security policies and procedures to ensure compliance and effectiveness.
By following these best practices, organizations can significantly enhance their perimeter security, protecting against both physical and digital threats.
Kiểm Tra Chu Vi - Video Hướng Dẫn Toàn Diện
READ MORE:
Thưởng thức nhạc phim từ Hans Zimmer trong bộ phim 'Góa Phụ' với bản nhạc 'Kiểm Tra Chu Vi'. Âm nhạc hấp dẫn và lôi cuốn.
Nhạc Phim Góa Phụ - "Kiểm Tra Chu Vi" - Hans Zimmer