Topic outer perimeter: The concept of the outer perimeter plays a crucial role in various fields, from enhancing security measures to aiding urban planning. This article delves into the multifaceted applications of the outer perimeter, exploring its significance in different contexts and highlighting advancements and future trends. Discover how effective perimeter management can transform safety and development strategies.
Table of Content
- Overview of Outer Perimeter
- Introduction
- Urban Planning and Infrastructure
- Security Applications
- Mathematical and Geometric Context
- Military and Strategic Uses
- Environmental and Ecological Impact
- Technological Advancements in Perimeter Security
- Historical Development and Changes
- Case Studies and Real-world Examples
- Future Trends and Predictions
- YOUTUBE: Khám phá album 'Vùng Ngoài Biên' của Tiên Tri phát hành năm 1998. Âm nhạc độc đáo và cuốn hút sẽ đưa bạn vào hành trình đầy cảm xúc.
Overview of Outer Perimeter
The term "outer perimeter" can refer to various contexts, including security, urban planning, and specific infrastructure projects. Below, we explore the diverse applications and significance of the outer perimeter.
1. Urban Planning and Infrastructure
In urban planning, the outer perimeter often refers to a highway or road encircling a city. A notable example is the proposed Outer Perimeter Highway around Atlanta, Georgia, intended to alleviate traffic congestion and promote regional connectivity.
- Original plan to encircle Atlanta about 20-25 miles outside Interstate 285.
- Designed to pass through or near several communities including Cartersville, Canton, and Buford.
- Later plans included the Northern Arc, focusing on a toll road to manage traffic and development.
2. Security Applications
The outer perimeter in security contexts defines the boundary of a property or facility. Effective perimeter security is crucial for preventing unauthorized access and ensuring the safety of the premises.
- Outer Perimeter Security
- Involves fences, gates, and barriers to control entry.
- May include surveillance systems and security personnel.
- Inner Perimeter Security
- Secures building entrances, windows, and internal access points.
- Utilizes locks, access control systems, and alarms.
- Interior Security
- Focuses on protecting internal spaces within the facility.
- Employs security cameras, motion detectors, and visitor management systems.
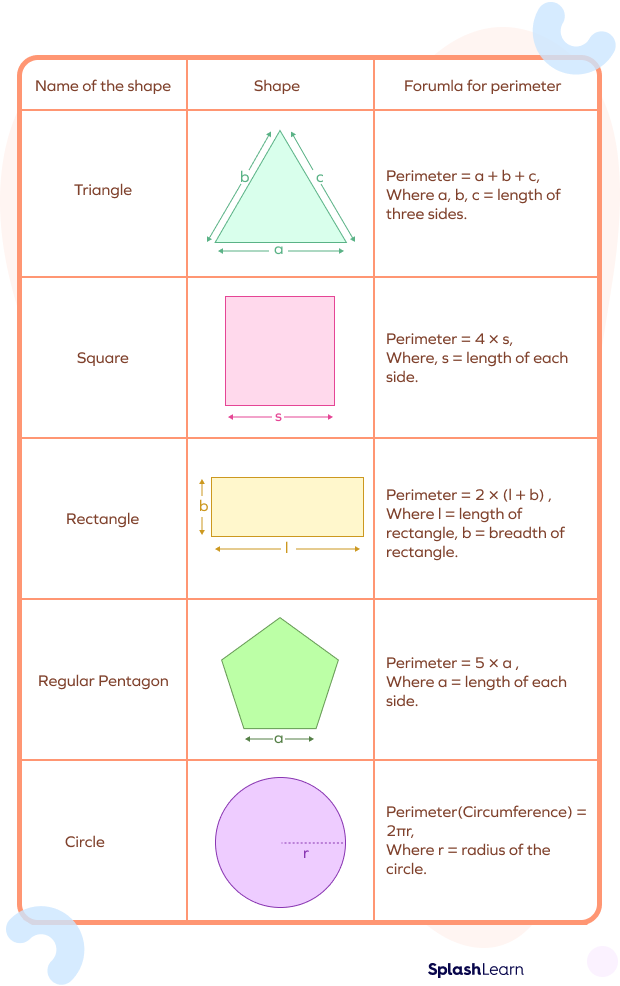
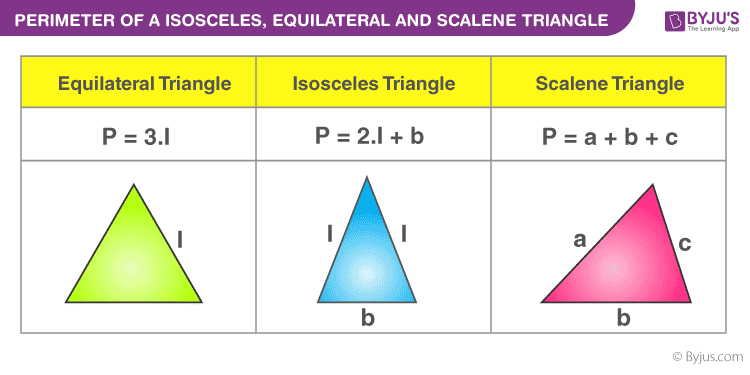
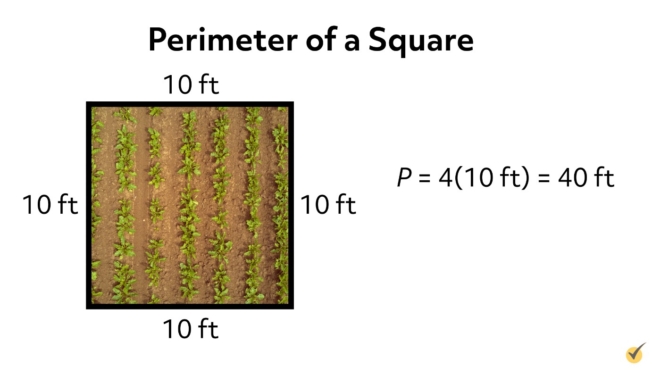
3. Mathematical and Geometric Context
In mathematics, the outer perimeter can refer to the boundary length of a geometric shape. For a polygon, it is the sum of the lengths of all its sides.
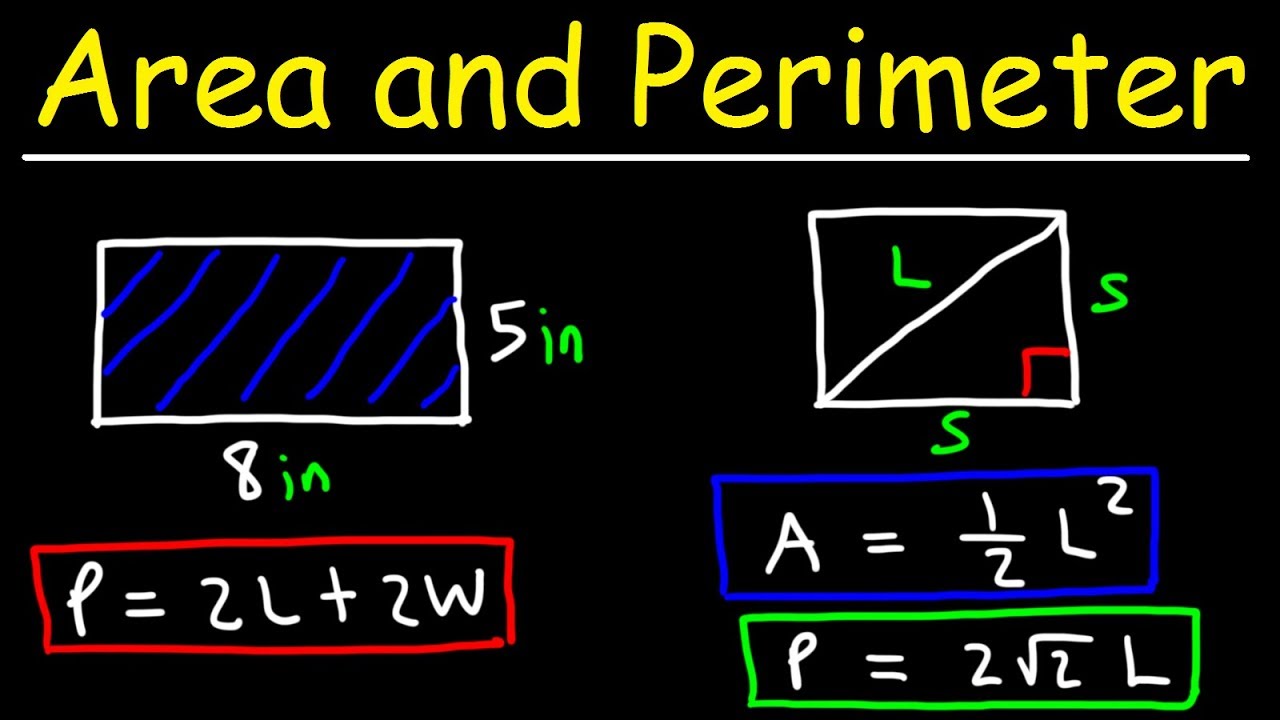
For example, the perimeter \( P \) of a rectangle with length \( l \) and width \( w \) is given by:
\[ P = 2l + 2w \]
4. Military and Strategic Uses
In military terms, the outer perimeter often defines the boundary of a defended area. It is crucial for setting up defensive positions and monitoring potential threats.
- Establishing checkpoints and surveillance posts.
- Deploying patrols and quick response teams to secure the perimeter.
Conclusion
The concept of the outer perimeter is versatile, spanning multiple fields from urban development to security and mathematics. Its effective management and design are essential for enhancing operational efficiency and safety in various contexts.

READ MORE:
Introduction
The term "outer perimeter" often refers to the boundary or outermost edge of a defined area, which can have various applications depending on the context. In security, it relates to the protective measures around a location, such as a building or property. In mathematics, it is the distance around a shape, crucial for understanding geometry and space calculations. This introduction provides an overview of the concept and its importance in different fields.
Urban Planning and Infrastructure
Urban planning and infrastructure development involve the strategic design and organization of urban spaces to support sustainable growth and improve the quality of life for residents. The concept of the outer perimeter plays a crucial role in this process, influencing how cities expand and manage their boundaries.
- Peri-Urbanization
- Green Infrastructure
- Urban Mobility
- Environmental Sustainability
- Participatory Planning
Peri-urbanization is the process of transforming rural land into urban areas, leading to the development of housing, transport routes, industrial zones, and recreational areas. This transition creates a dynamic interface between urban and rural spaces, necessitating careful planning to balance growth and sustainability.
Green infrastructure refers to the integration of natural systems into urban planning. Examples include the development of parks, green corridors, and permeable pavements that mitigate flooding, enhance biodiversity, and provide recreational spaces for residents. These projects help cities manage stormwater, reduce heat islands, and improve air quality.
Effective urban mobility solutions are essential for the development of peripheral areas. This includes creating efficient public transport networks that connect the outer perimeter with the city center, reducing traffic congestion and promoting sustainable travel options.
Environmental sustainability is a key consideration in urban planning. Strategies include incorporating renewable energy sources, protecting natural habitats, and ensuring that new developments adhere to environmental regulations. This approach helps reduce the ecological footprint of urban areas and promotes long-term resilience.
Engaging the community in the planning process ensures that the needs and perspectives of residents are considered. Participatory planning fosters collaboration between government bodies, private sector stakeholders, and citizens, leading to more inclusive and effective urban development outcomes.
Security Applications
Outer perimeter security is vital for protecting various types of facilities and properties from unauthorized access, intrusions, and threats. Security applications for outer perimeters encompass a range of technologies and strategies designed to deter, detect, and respond to potential security breaches.
Some common security applications for outer perimeters include:
- Physical Barriers: Erecting walls, fences, or barricades around the perimeter to prevent unauthorized entry.
- Access Control Systems: Implementing mechanisms such as gates, turnstiles, or biometric scanners to regulate entry and exit points.
- Surveillance Systems: Deploying cameras, sensors, and other monitoring devices to continuously monitor the perimeter and detect any suspicious activity.
- Intrusion Detection Systems (IDS): Installing sensors and alarms that trigger alerts when unauthorized access or intrusion attempts are detected.
- Perimeter Lighting: Illuminating the perimeter area to enhance visibility and deter potential intruders, especially during nighttime.
- Security Patrols: Conducting regular patrols or utilizing security personnel to visually inspect the perimeter and respond to any security incidents.
Furthermore, advancements in technology have led to the development of integrated security solutions that combine various components such as access control, surveillance, and analytics to provide comprehensive perimeter protection.
Effective security applications for outer perimeters require careful planning, integration, and maintenance to ensure optimal performance and protection against evolving security threats.
Mathematical and Geometric Context
The mathematical and geometric context of outer perimeters plays a crucial role in understanding and designing effective security measures. By analyzing the spatial characteristics and applying mathematical principles, security professionals can optimize the layout and configuration of perimeter defenses.
Key aspects of the mathematical and geometric context include:
- Area Calculation: Utilizing mathematical formulas to calculate the total area enclosed by the outer perimeter, which influences the allocation of resources for surveillance and patrol.
- Distance and Proximity: Determining the distances between key points of interest, such as entry/exit gates, security checkpoints, and critical infrastructure, to optimize response times and coverage.
- Angle of Visibility: Analyzing the line of sight and angles of visibility from observation points to identify potential blind spots and optimize the placement of surveillance cameras and sensors.
- Perimeter Shape: Considering the shape of the outer perimeter, whether it's linear, rectangular, or irregular, to design appropriate security measures that account for potential vulnerabilities.
- Barrier Effectiveness: Evaluating the effectiveness of physical barriers in deterring intrusions by assessing factors such as height, material strength, and structural integrity.
Furthermore, geometric principles such as triangulation and Voronoi diagrams can be employed to enhance the accuracy and efficiency of security operations within the outer perimeter.
By integrating mathematical analysis and geometric optimization techniques, security professionals can develop robust strategies for securing outer perimeters and mitigating security risks effectively.
Military and Strategic Uses
The outer perimeter serves critical military and strategic purposes, playing a pivotal role in defending military installations, strategic assets, and national borders. Military forces employ a variety of tactics and technologies to secure outer perimeters and maintain operational readiness.
Key military and strategic uses of outer perimeters include:
- Force Protection: Establishing secure outer perimeters to safeguard military bases, airfields, and naval installations from external threats such as enemy incursions, sabotage, and terrorist attacks.
- Border Security: Deploying border fences, barriers, and surveillance systems along national borders to prevent unauthorized crossings, smuggling, and illegal activities.
- Asset Protection: Securing strategic assets such as command centers, communication facilities, and ammunition depots within fortified outer perimeters to deter theft, espionage, and sabotage.
- Strategic Positioning: Utilizing outer perimeters to establish defensive positions, observation posts, and forward operating bases to monitor and control key areas of interest.
- Force Projection: Extending outer perimeters beyond immediate installations to create buffer zones and control the surrounding territory, enhancing strategic depth and maneuverability.
- Intelligence Gathering: Leveraging surveillance technologies and reconnaissance assets to gather intelligence on enemy activities, movements, and intentions along the outer perimeter.
Furthermore, outer perimeter security is integrated with military doctrine, training, and contingency planning to ensure rapid response capabilities and resilience against emerging threats.
Effective military and strategic uses of outer perimeters require continuous evaluation, adaptation, and coordination across various branches of the armed forces to uphold national security interests.
Environmental and Ecological Impact
The implementation of outer perimeter security measures can have significant environmental and ecological impacts, affecting local ecosystems, wildlife habitats, and natural resources. It is essential to consider these factors when designing and deploying security solutions to minimize adverse effects and promote sustainability.
Some of the environmental and ecological impacts associated with outer perimeter security include:
- Habitat Fragmentation: Construction of fences, walls, or barriers can fragment natural habitats, disrupting wildlife corridors and migration routes, and limiting access to essential resources such as food and water.
- Species Displacement: Installation of security infrastructure may force wildlife species to relocate or alter their behavior patterns, leading to conflicts with human populations or increased vulnerability to predation.
- Soil and Vegetation Disturbance: Clearing land and altering vegetation for security purposes can result in soil erosion, loss of biodiversity, and degradation of ecosystem services such as carbon sequestration and water filtration.
- Water Resource Management: Construction activities associated with outer perimeter security may impact water bodies through pollution, sedimentation, or alteration of hydrological processes, affecting aquatic ecosystems and downstream communities.
- Light and Noise Pollution: Illumination and operational activities along the outer perimeter can contribute to light pollution, disrupting natural light cycles and nocturnal behaviors of wildlife, while noise from security operations may disturb sensitive species.
Addressing the environmental and ecological impacts of outer perimeter security requires adopting mitigation measures and incorporating eco-friendly design principles into security infrastructure projects. This may include:
- Green Infrastructure: Integrating natural elements such as green walls, vegetative barriers, and wildlife crossings into security designs to mitigate habitat fragmentation and promote biodiversity.
- Sustainable Land Management: Implementing erosion control measures, reforestation efforts, and sustainable landscaping practices to restore and enhance ecological resilience in affected areas.
- Wildlife Monitoring and Conservation: Conducting ecological surveys, habitat assessments, and wildlife monitoring programs to track the impact of security measures on local fauna and implement adaptive management strategies.
- Community Engagement: Collaborating with local stakeholders, conservation organizations, and indigenous communities to foster dialogue, raise awareness, and incorporate traditional ecological knowledge into security planning and decision-making processes.
By integrating environmental considerations into outer perimeter security planning and implementation, it is possible to achieve a balance between security needs and ecological sustainability, ensuring the long-term health and resilience of both human and natural systems.
Technological Advancements in Perimeter Security
Technological innovations have revolutionized perimeter security, offering enhanced capabilities for detection, surveillance, and response to potential threats along outer perimeters. These advancements empower security professionals to better protect assets, infrastructure, and personnel against evolving security challenges.
Some of the notable technological advancements in perimeter security include:
- Video Analytics: Utilizing advanced algorithms and AI-powered video analytics to detect and analyze anomalies in real-time footage, enabling proactive threat identification and response.
- Unmanned Aerial Vehicles (UAVs): Deploying drones equipped with cameras, sensors, and thermal imaging capabilities to conduct aerial surveillance and reconnaissance of expansive perimeter areas.
- Radar Systems: Employing radar technology to detect and track intrusions beyond line-of-sight, providing early warning of approaching threats and enabling rapid response.
- Perimeter Intrusion Detection Systems (PIDS): Integrating sensors, vibration detectors, and seismic sensors to create virtual tripwires and detect unauthorized movements along the outer perimeter.
- Biometric Access Control: Implementing biometric authentication methods such as fingerprint scanners, facial recognition systems, and iris scanners to enhance access control and prevent unauthorized entry.
- Smart Fencing: Deploying electrified fences or smart barriers equipped with sensors and alarms to detect tampering or attempted breaches, while minimizing false alarms.
Furthermore, the convergence of technologies such as IoT (Internet of Things), cloud computing, and data analytics enables seamless integration and interoperability of perimeter security systems, providing a holistic approach to threat detection and mitigation.
As technology continues to evolve, future advancements in perimeter security may include the use of machine learning algorithms for predictive analytics, autonomous security robots for patrolling, and blockchain technology for secure data transmission and authentication.
Overall, technological advancements play a pivotal role in enhancing the effectiveness, efficiency, and scalability of perimeter security solutions, empowering organizations to adapt and respond to emerging security threats with greater agility and precision.
Historical Development and Changes
The historical development of outer perimeter security reflects the evolution of human civilization, from early rudimentary fortifications to modern-day high-tech defense systems. Over time, advancements in warfare, technology, and strategic thinking have shaped the design, function, and effectiveness of perimeter defenses.
Key historical developments and changes in outer perimeter security include:
- Ancient Fortifications: Throughout history, civilizations have constructed walls, moats, and ramparts around cities, palaces, and military outposts to protect against external threats such as invasions, raids, and sieges.
- Medieval Castles: During the Middle Ages, feudal lords and monarchs built castles with thick stone walls, drawbridges, and towers to defend against enemy attacks and maintain control over territories.
- Colonial Fortifications: European colonial powers established coastal forts, trading posts, and garrisons in distant lands to secure maritime trade routes and expand their empires, often facing resistance from indigenous populations.
- World Wars: The 20th century witnessed the use of barbed wire, trenches, and bunkers as defensive measures during World War I, followed by the development of sophisticated perimeter defenses, radar systems, and anti-aircraft guns in World War II.
- Cold War Era: The Cold War era saw the proliferation of border fences, minefields, and surveillance technologies along ideological dividing lines, such as the Iron Curtain in Europe and the Korean Demilitarized Zone.
- Modern Security Challenges: In the 21st century, outer perimeter security faces new challenges posed by terrorism, cyber threats, and asymmetric warfare, leading to the adoption of integrated security systems, biometric authentication, and cyber defenses.
Furthermore, shifts in geopolitical dynamics, urbanization patterns, and technological innovation continue to influence the development of outer perimeter security strategies and solutions.
By studying the historical development and changes in outer perimeter security, we gain insights into the enduring importance of defending borders, safeguarding assets, and preserving territorial integrity in an ever-changing world.

Case Studies and Real-world Examples
Examining case studies and real-world examples of outer perimeter security implementations provides valuable insights into effective strategies, challenges encountered, and lessons learned in safeguarding diverse environments and assets.
Some notable case studies and real-world examples of outer perimeter security include:
- The Great Wall of China: Dating back over two millennia, the Great Wall of China stands as one of the most iconic and enduring examples of outer perimeter security. Constructed to protect against nomadic invasions, the wall stretches thousands of kilometers across rugged terrain, featuring watchtowers, fortresses, and defensive bastions.
- Fortified Borders: Countries around the world have implemented fortified borders and barriers to secure national boundaries and regulate cross-border movements. Examples include the Israel–Gaza barrier, the United States–Mexico border fence, and the India–Pakistan Line of Control.
- Military Installations: Military bases and installations deploy advanced perimeter security measures to protect sensitive assets and personnel. Case studies may include Fort Knox in the United States, Camp Bastion in Afghanistan, and Naval Station Pearl Harbor in Hawaii.
- Critical Infrastructure: Key infrastructure facilities such as power plants, airports, and seaports rely on robust perimeter security to mitigate risks of sabotage, terrorism, and industrial espionage. Real-world examples may involve the security measures implemented at the Three Gorges Dam in China, Heathrow Airport in the United Kingdom, and the Port of Singapore.
- Corporate Campuses: Large corporations and tech giants invest in perimeter security solutions to protect corporate campuses, data centers, and research facilities. Case studies may feature the security infrastructure deployed by companies like Google, Apple, and Amazon at their headquarters and regional offices.
- High-security Prisons: Correctional facilities implement stringent perimeter security measures to prevent escapes and unauthorized access. Examples may include maximum-security prisons such as ADX Florence in the United States, Alcatraz Federal Penitentiary, and HMP Belmarsh in the United Kingdom.
These case studies and real-world examples demonstrate the diverse applications and varying levels of complexity involved in outer perimeter security across different contexts and environments.
Future Trends and Predictions
The future of outer perimeter security is shaped by emerging technologies, evolving threats, and changing societal dynamics, driving the development of innovative strategies and solutions to address complex security challenges.
Some future trends and predictions in outer perimeter security include:
- Integration of Artificial Intelligence: AI-powered analytics and machine learning algorithms will play an increasingly vital role in perimeter security, enabling autonomous threat detection, behavior analysis, and decision-making capabilities.
- Enhanced Sensor Technologies: Advancements in sensor technologies, including hyperspectral imaging, LiDAR, and acoustic sensors, will enable more precise and comprehensive monitoring of outer perimeters, detecting subtle changes and anomalies with greater accuracy.
- Drone-based Security Solutions: The use of drones equipped with advanced sensors and AI algorithms will revolutionize perimeter surveillance, providing flexible, cost-effective, and scalable monitoring capabilities for large-scale facilities and remote areas.
- Biometric Authentication: Biometric authentication methods such as gait recognition, vein pattern recognition, and brainwave authentication will enhance access control and identity verification at outer perimeter entry points, reducing reliance on traditional credentials.
- Cyber-Physical Security Convergence: The convergence of physical security and cybersecurity domains will become increasingly prevalent, with integrated solutions combining digital threat intelligence, network security, and physical access controls to safeguard outer perimeters from cyber-physical threats.
- Resilience and Adaptability: Outer perimeter security strategies will prioritize resilience and adaptability, with modular, scalable, and agile security architectures capable of dynamically adjusting to evolving threats and operational requirements.
Furthermore, the proliferation of smart cities, critical infrastructure digitization, and global connectivity will present both opportunities and challenges for outer perimeter security, requiring holistic, multi-disciplinary approaches to safeguarding assets and communities.
By anticipating future trends and embracing innovation, organizations can stay ahead of emerging threats and effectively protect their outer perimeters in an increasingly complex and interconnected world.
Khám phá album 'Vùng Ngoài Biên' của Tiên Tri phát hành năm 1998. Âm nhạc độc đáo và cuốn hút sẽ đưa bạn vào hành trình đầy cảm xúc.
Tiên Tri - Vùng Ngoài Biên (Album Đầy Đủ 1998)
READ MORE:
Khám phá 'Vùng Ngoài Biên' với nhạc ngủ tập trung chất lượng 4K. Âm nhạc êm dịu giúp bạn dễ dàng thư giãn và tập trung.
VÙNG NGOÀI BIÊN | Nhạc Ngủ Tập Trung 4K